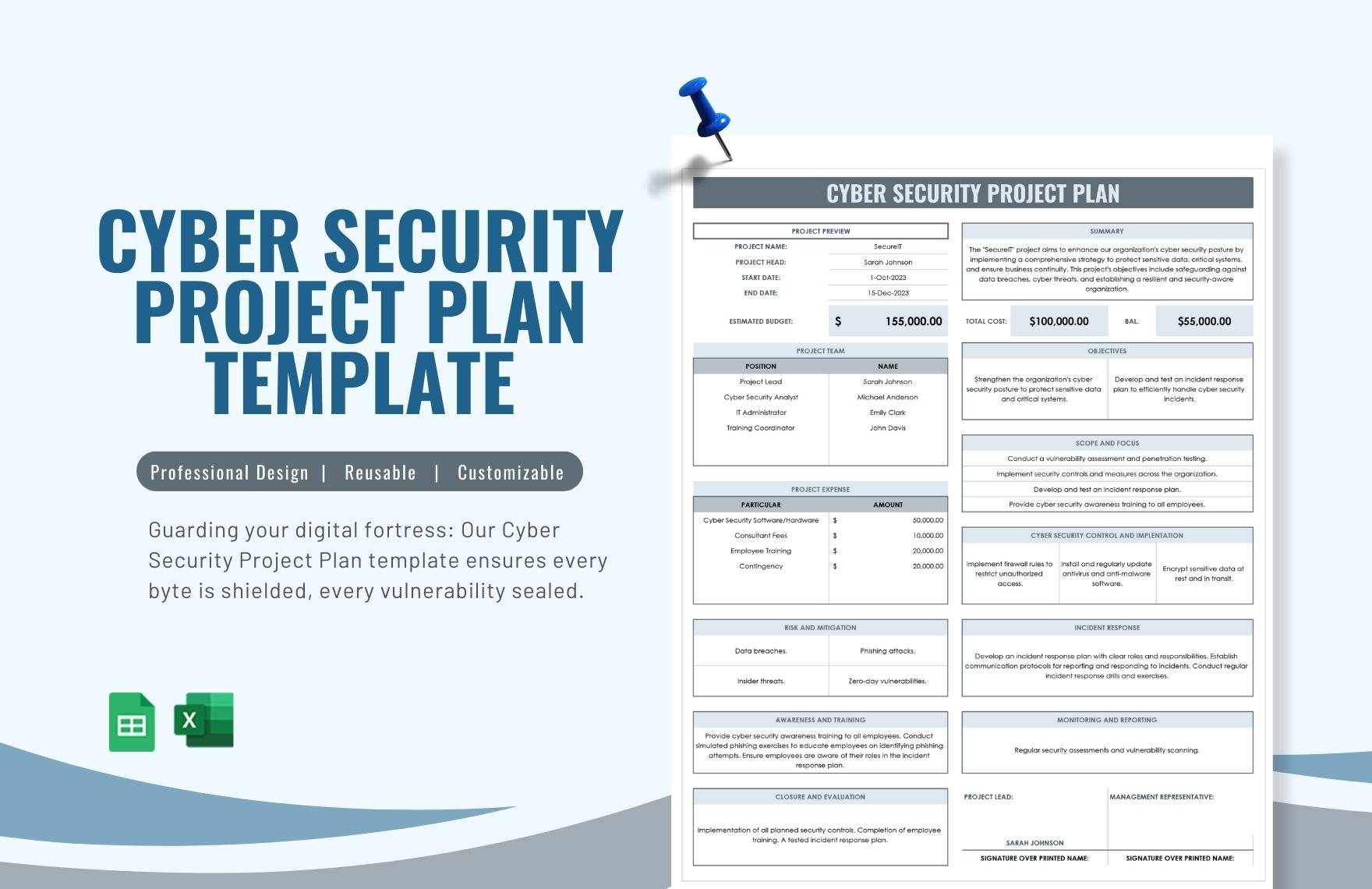
Cyber Security Implementation Plan Template - These will continue to be. A cybersecurity plan specifies the policies, processes, and controls required to protect an. Made in the usaeditable word documents The policy templates are provided courtesy of the state of new york and the state of california. Use this information to complete your plan, prioritise which recommendations you will. Cip guidance and templates can be found on this page.
Made in the usaeditable word documents These will continue to be. A cybersecurity plan specifies the policies, processes, and controls required to protect an. Use this information to complete your plan, prioritise which recommendations you will. The policy templates are provided courtesy of the state of new york and the state of california. Cip guidance and templates can be found on this page.
Cip guidance and templates can be found on this page. A cybersecurity plan specifies the policies, processes, and controls required to protect an. Use this information to complete your plan, prioritise which recommendations you will. Made in the usaeditable word documents The policy templates are provided courtesy of the state of new york and the state of california. These will continue to be.
Cyber Security Implementation Plan Template
A cybersecurity plan specifies the policies, processes, and controls required to protect an. Cip guidance and templates can be found on this page. Use this information to complete your plan, prioritise which recommendations you will. These will continue to be. Made in the usaeditable word documents
Cyber Security Risk Management Plan Template
Cip guidance and templates can be found on this page. A cybersecurity plan specifies the policies, processes, and controls required to protect an. These will continue to be. Made in the usaeditable word documents The policy templates are provided courtesy of the state of new york and the state of california.
Cyber Security Implementation Plan Template
A cybersecurity plan specifies the policies, processes, and controls required to protect an. The policy templates are provided courtesy of the state of new york and the state of california. Made in the usaeditable word documents Use this information to complete your plan, prioritise which recommendations you will. These will continue to be.
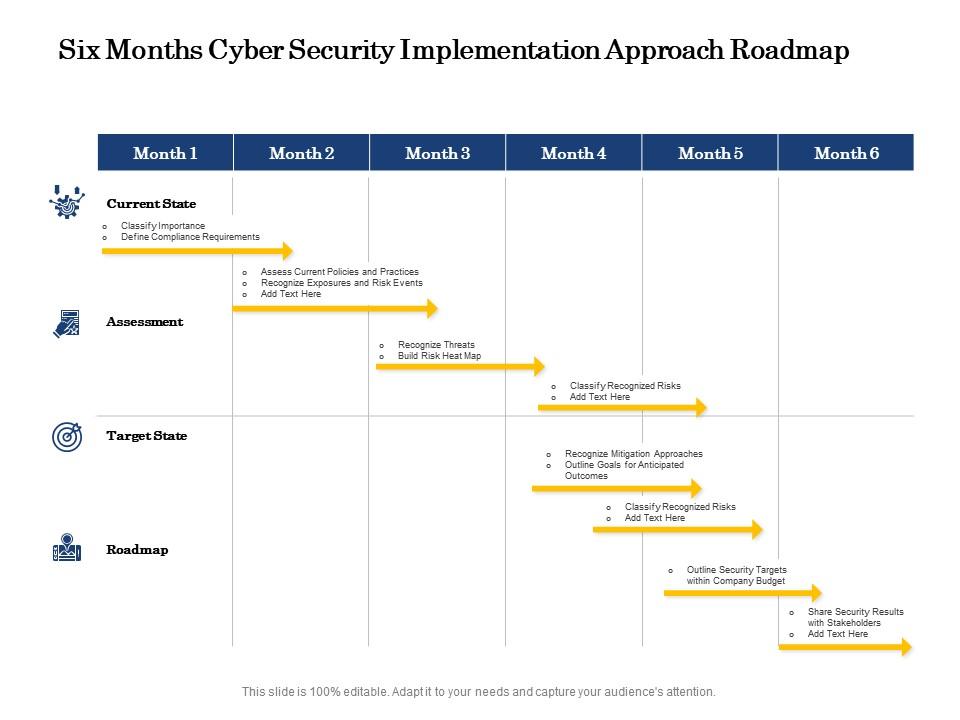
Top 10 Templates to Fabricate a Powerful Cyber Security Roadmap [Free
Made in the usaeditable word documents These will continue to be. Cip guidance and templates can be found on this page. A cybersecurity plan specifies the policies, processes, and controls required to protect an. The policy templates are provided courtesy of the state of new york and the state of california.
Cyber Security Implementation Plan Template
Use this information to complete your plan, prioritise which recommendations you will. A cybersecurity plan specifies the policies, processes, and controls required to protect an. Made in the usaeditable word documents The policy templates are provided courtesy of the state of new york and the state of california. These will continue to be.
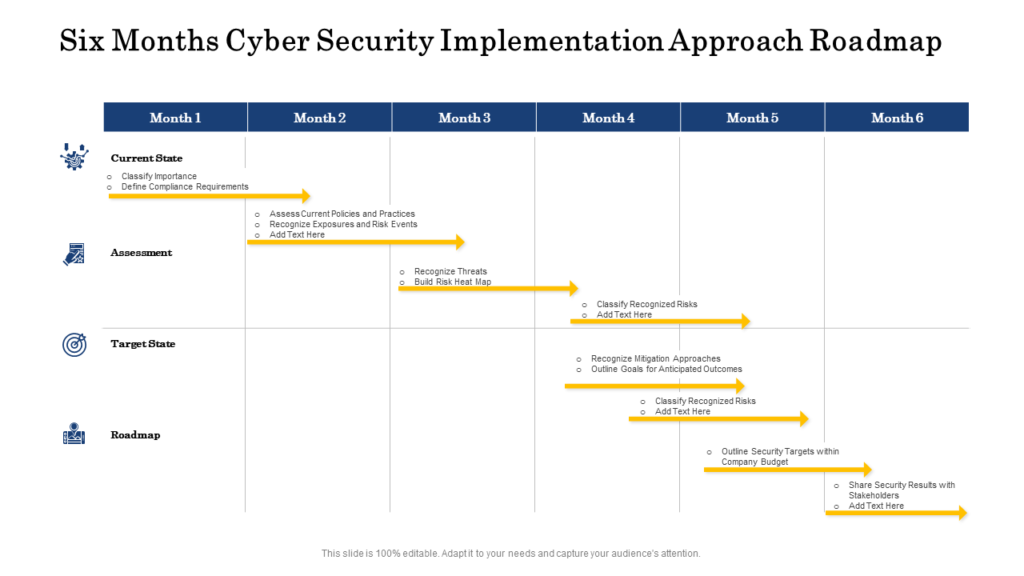
Cybersecurity Strategy Template
The policy templates are provided courtesy of the state of new york and the state of california. Cip guidance and templates can be found on this page. Use this information to complete your plan, prioritise which recommendations you will. A cybersecurity plan specifies the policies, processes, and controls required to protect an. Made in the usaeditable word documents
Cyber Security Implementation Plan Template
Cip guidance and templates can be found on this page. Use this information to complete your plan, prioritise which recommendations you will. These will continue to be. The policy templates are provided courtesy of the state of new york and the state of california. Made in the usaeditable word documents
Must Have Cyber Security Strategic Plan Templates with Samples and Examples
A cybersecurity plan specifies the policies, processes, and controls required to protect an. These will continue to be. Cip guidance and templates can be found on this page. Use this information to complete your plan, prioritise which recommendations you will. The policy templates are provided courtesy of the state of new york and the state of california.
FREE Cyber Security Templates & Examples Edit Online & Download
Made in the usaeditable word documents A cybersecurity plan specifies the policies, processes, and controls required to protect an. The policy templates are provided courtesy of the state of new york and the state of california. Cip guidance and templates can be found on this page. These will continue to be.
Free Cybersecurity Implementation Plan Template to Edit Online
These will continue to be. Cip guidance and templates can be found on this page. A cybersecurity plan specifies the policies, processes, and controls required to protect an. The policy templates are provided courtesy of the state of new york and the state of california. Made in the usaeditable word documents
The Policy Templates Are Provided Courtesy Of The State Of New York And The State Of California.
Made in the usaeditable word documents Cip guidance and templates can be found on this page. These will continue to be. A cybersecurity plan specifies the policies, processes, and controls required to protect an.